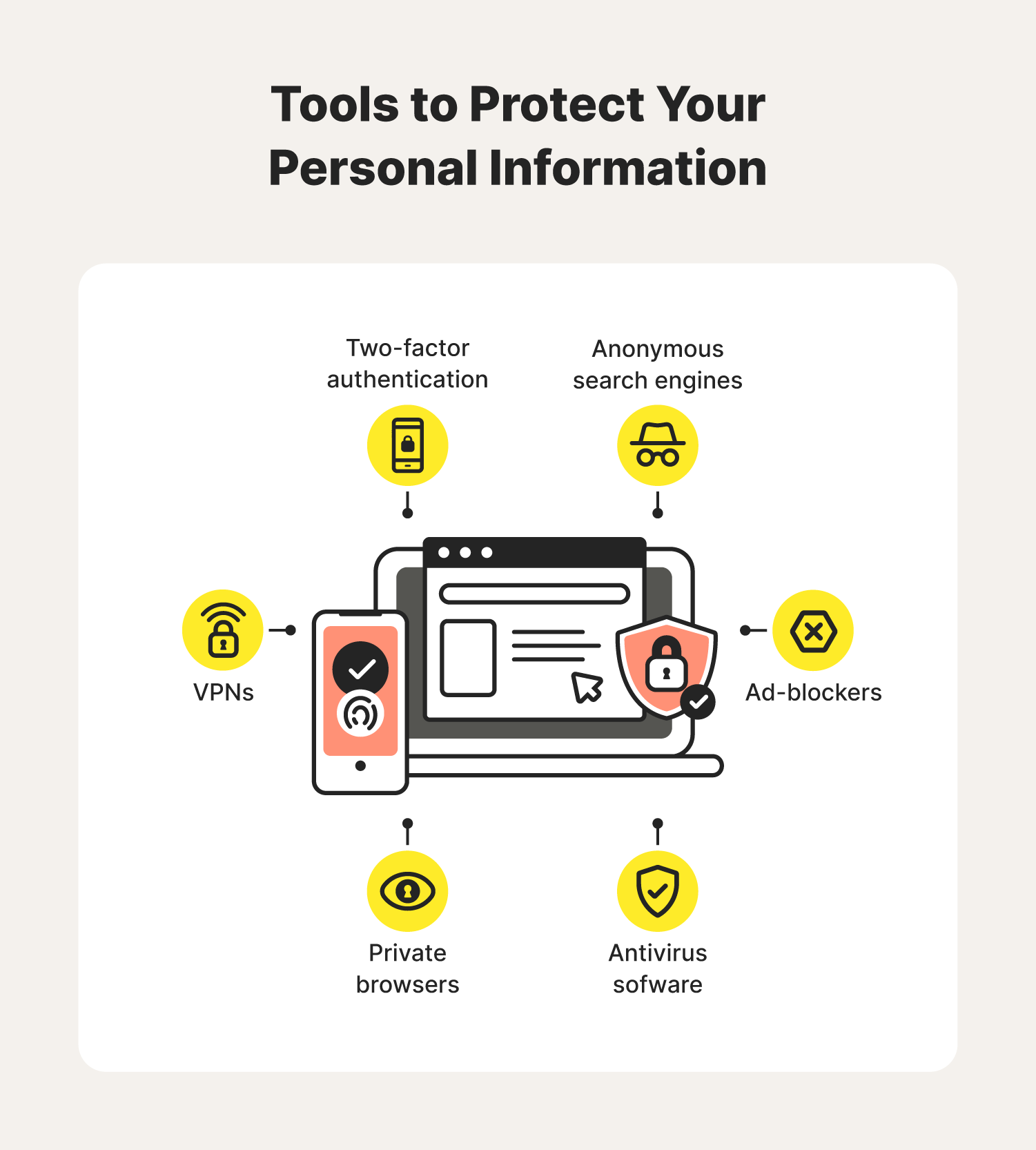
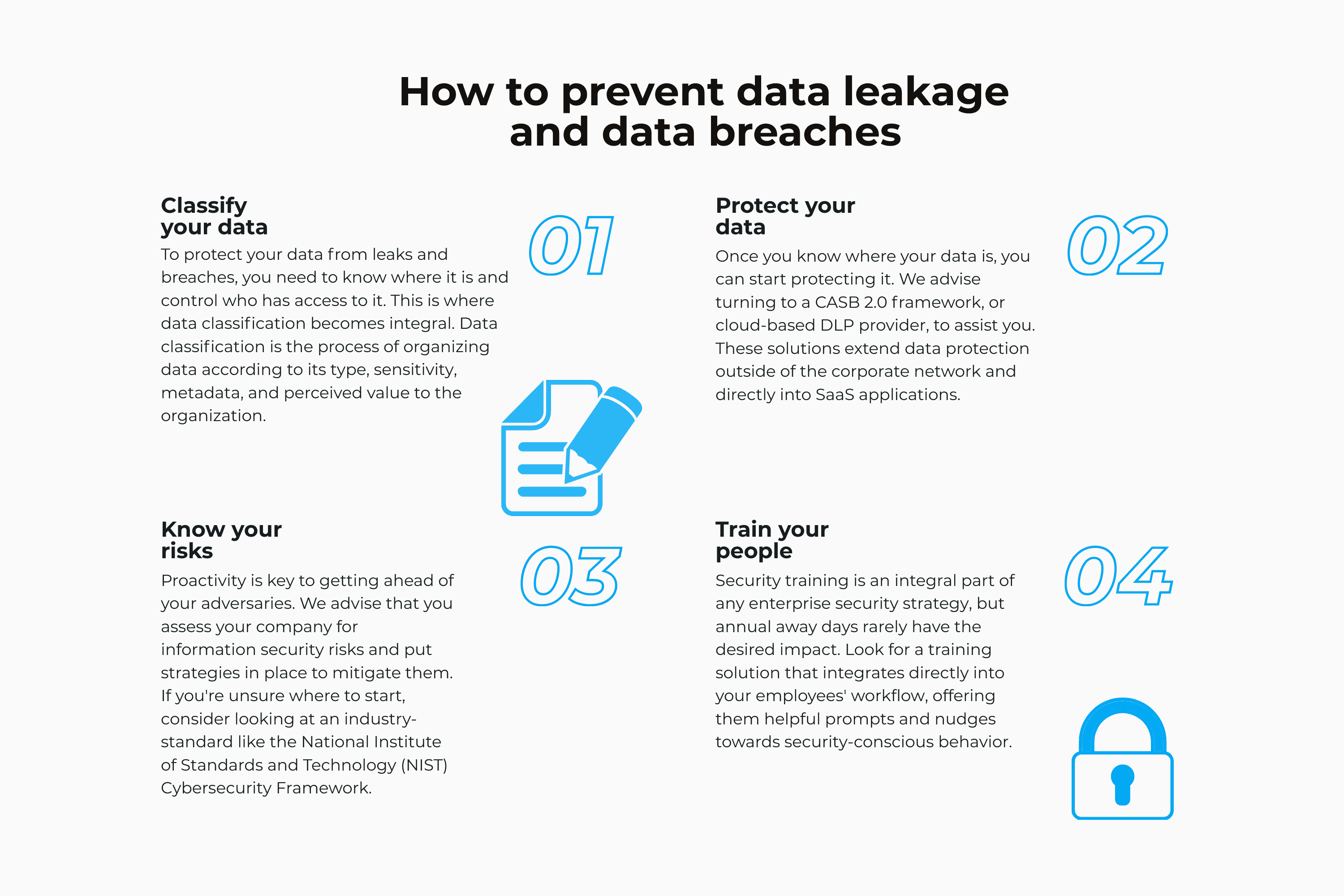
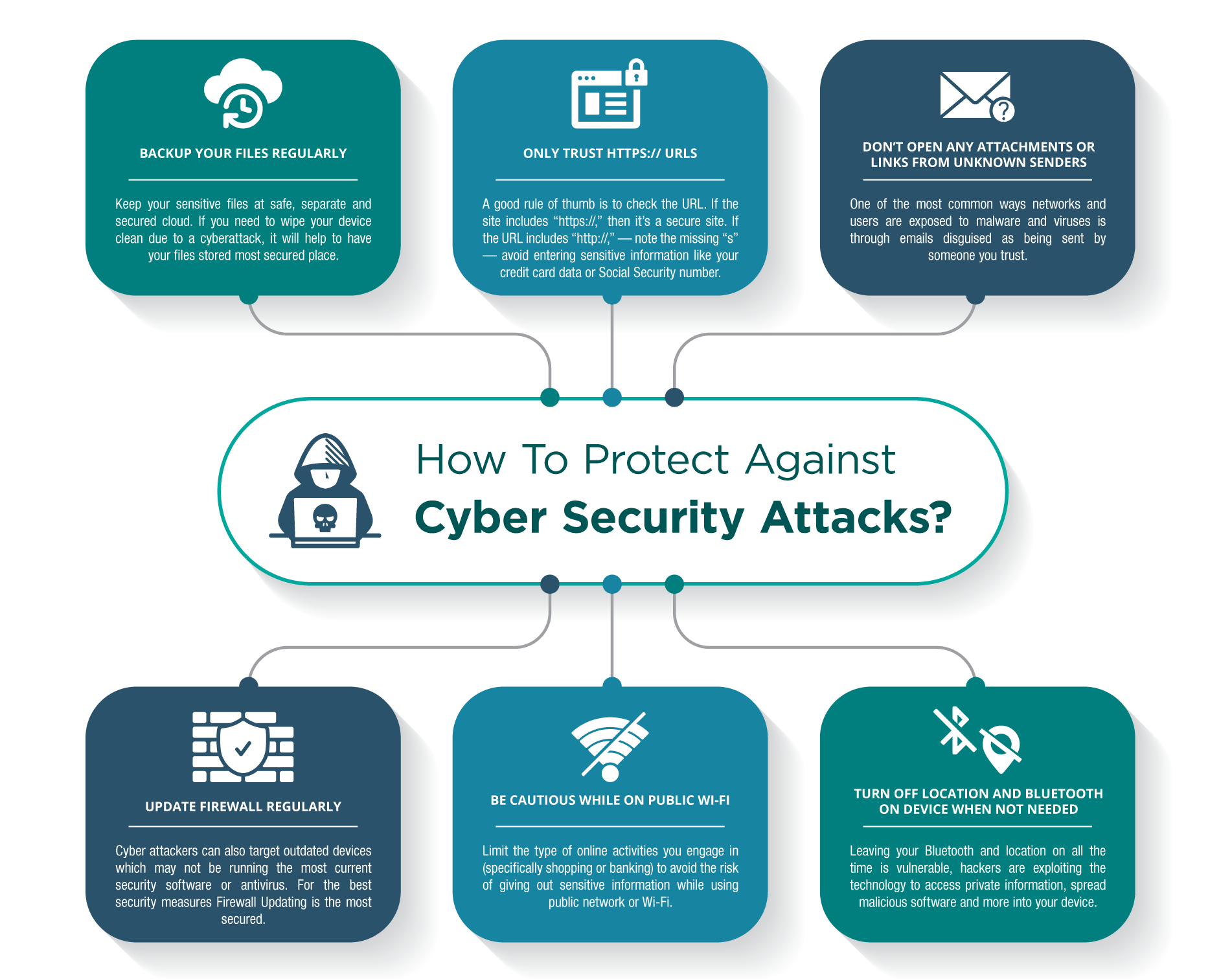
Learn how data leaks occur and discover the best practices to safeguard your personal information and online privacy.
The Aiminghigher Leaks: Protecting Your Online Privacy
Learn how data leaks occur and discover the best practices to safeguard your personal information and online privacy....